问题:
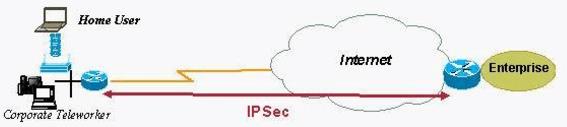
Refer to the exhibit. An enterprise's security policy disallows the use of wireless on a Teleworker PC. Choose the most appropriate 830 security feature to use to enforce the security policy.()
A . 802.1X authentication
B . authentication proxy
C . Context Based Access Control
D . Lock and Key authenticatio
Refer to the exhibit. An enterprise's security policy disallows the use of wireless on a Teleworker PC. Choose the most appropriate 830 security feature to use to enforce the security policy.()

● 参考解析
本题暂无解析
相关内容
相关标签